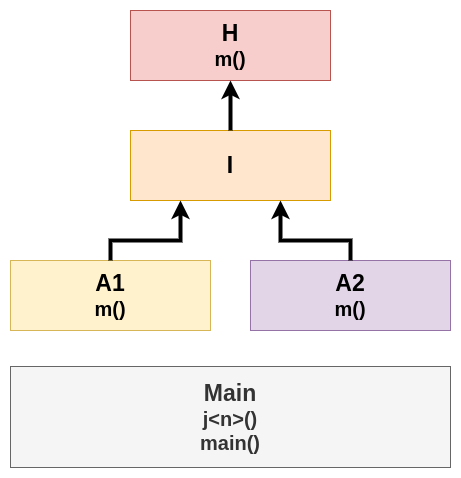
In our previous article Callsite resolution in the JVM we discussed how a monomorphic callsite looks like after inline caching:
|
1
2
3
|
public static void j2(I i) throws Throwable {
i.m();
}
|
Java
|
1
2
3
4
|
...
0x7f5db4e0b7cd: movabs $0x801000400,%rax
0x7f5db4e0b7d7: callq 0x7fffe55f9800
..
|
x86_64 assembly (generated by C1)
As a reminder, the RAX register is loaded with the Klass* for which the optimization is valid: a receiver object of the A1 type. The callq instruction that follows goes to the unverified entry of the A1::m method, where the Klass* in RAX is checked against the receiver object’s class. If the check succeeds, execution proceeds to the actual method. In this article we will see what happens when the check fails or, in other words, when the receiver object is not an instance of A1 and the optimization is not longer valid.
Continue reading “Monomorphic to megamorphic callsite in C1”


 ) at
) at