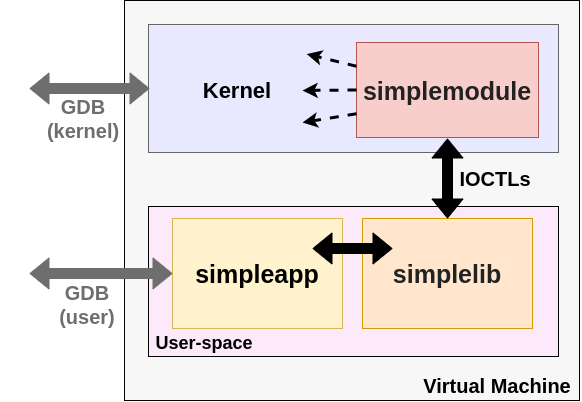
In the context of the Open Source Study Group, we decided to explore some Linux kernel APIs related to IPC and namespaces. An effective approach to this is exercising APIs from a crafted user-space application, while debugging at the kernel level. After some progress and setting breakpoints here and there, a challenge became evident: breakpoints in common functions are hit all the time from different processes. We need to filter out non-relevant hits, while staying focused on our application. This can be done, perhaps, by means of a conditional breakpoint in the debugger. Checking the binary image associated to the current task (looking into the mm_struct) should make it, but debugging complexity starts growing rapidly.
Continue reading “Simple App: a Linux toy application for user and kernel space”