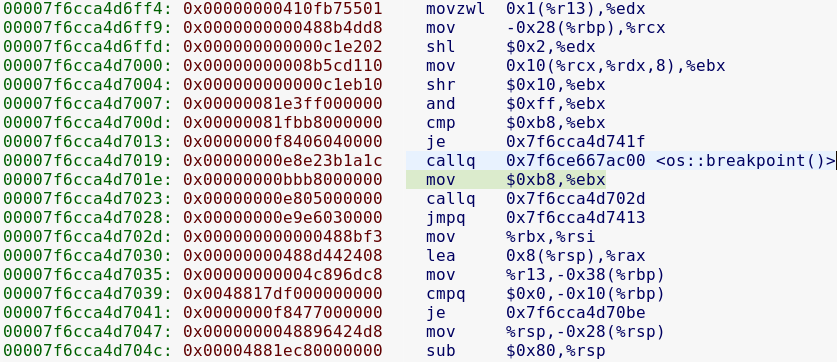
Quarkslab folks proposed a challenge: modify any compiler to generate code with some obfuscation but valid semantics. In other words, add some noise but keep the program logic valid.
Time to have some fun with C1: OpenJDK’s 1st tier JIT compiler.
Obfuscation “noise” can be added at different stages of the compilation process. Adding it early may be useful to target multiple architectures but it’s necessary to check if following optimization passes revert the effect.
Continue reading “Some noise to C1 JIT compiler for x86_64 (OpenJDK JVM – Hotspot)”